





Notes:
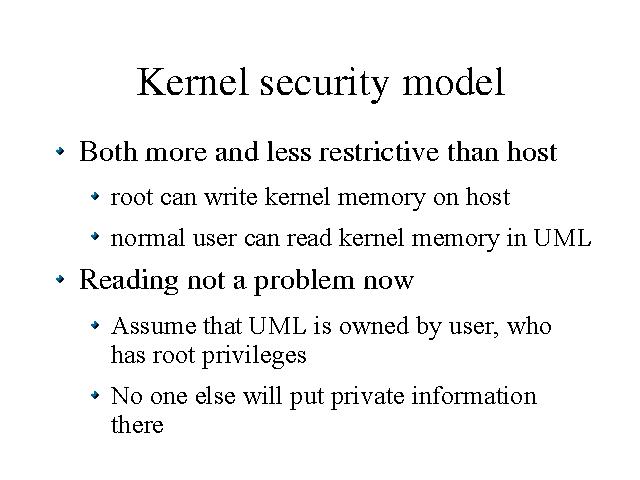
For now, UML jailing is concerned with protecting kernel data from being changed. Kernel data being read is not a concern at this point. Reading kernel data is not a security problem in the sense that it allows someone to break out of UML. We expect that the user inside UML has root privileges inside it, and so can read any data in the virtual machine anyway.
UML virtual machines are also single-user in the sense that they are typically assigned to a specific person and other people don't put their sensitive information in it. This makes security concerns such as sniffing personal email less of a problem.












